Flight plan
Description
After everything is cleared you start to wonder about the origin of this attack.
When inspecting the logs, a correlation between the start of the compromise and a pdf file arriving to the ATC can be made.
200pts
Question
Inspect the flight plan, find out if there is anything malicious hidden in it.
Solution
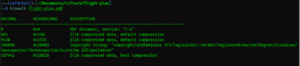
The task was to find a malicious application hidden in a pdf file. I first looked at the PDF file with the strings command, but that did not produce the desired result. Next I tried the binwalk application, which showed that there were other files inside the file. I used the command binwalk -e file.pdf. Since the binwalk file is run with root user privileges (the service provider's virtual machine is in root mode) the --run-as=root suffix must be used.
I looked at what the files contained and one file called 2DE26 was interesting. The SHA256Hash of the file indicated that it was a trojan. Virustotal Well luckily I am using the virtual machine for the task. I tried to run the file with wine, but as it is a 32 bit program wine refuses to start.
I will have a look with the strings command to see if there is a flag in plain text available.
I find the following line:
hxX htoBohCryp1hX ha394hcf15h8adehb84-h8c-ah2-42h-888h25f2h3a44h is hflag1
This is clearly a flag, but it is still messed up. I'm trying to find an app online that would change the number of letters in the right way. However, I can't find anything suitable, so I try to re-run the file by installing x86 architecture wine on the system. dpkg --add-architecture i386 && apt update && apt install wine32 wine
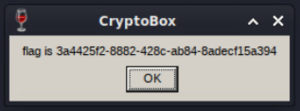
The application then agrees to start with the command wine [application]. The application will output the correct flag.
Tools
binwalk | binwalk -e file.pdf
wine
Flag
3a4425f2-8882-428c-ab84-8adecf15a394