SSID 2: Difference between revisions
From Pessin randon wiki
Created page with "===Description=== ===Question=== ===Solution=== ===Tools=== ===Flag=== ===Links=== * Back to CTF Challenges page" |
No edit summary |
||
| (3 intermediate revisions by one other user not shown) | |||
| Line 1: | Line 1: | ||
[[File:Ohje.PNG|thumb|How to add keys decryption keys to wireshark]] | |||
[[File:Stream6.PNG|thumb|Wireshark stream 6]] | |||
===Description=== | ===Description=== | ||
[[File:Flag.PNG|thumb|base64 decoded flag]] | |||
After cracking the wifi password in previous challenge, you can now start investigating the traffic in the pcap. | |||
100pts | |||
===Question=== | ===Question=== | ||
Analyse the pcap and find the flag. | |||
===Solution=== | ===Solution=== | ||
Insert wlan password as a WPA-PWD <code>pinkpanther</code>. You will find it at wireshark -> Edit -> Preferences -> Protocols -> IEEE 802.11 -> Decryption keys -> Edit | |||
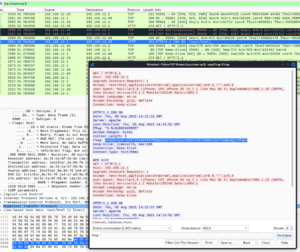
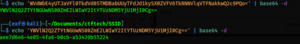
Then I just start to browse through packets and start with tcp streams. Using "Follow TCP stream" I just did go through streams one by one until I found something interestin. In stream 6 was http answer where was flag base64 encoded. So I decoded that and found that you have to encode it again. Until that I got the flag. | |||
===Tools=== | ===Tools=== | ||
* wireshark | |||
* echo | |||
* base64 | |||
===Flag=== | ===Flag=== | ||
<code>aee7d6e6-4e05-4fa6-b0cb-a53439b55224</code> | |||
===Links=== | ===Links=== | ||
*[[CTF Challenges | Back to CTF Challenges page]] | *[[CTF Challenges | Back to CTF Challenges page]] | ||
Latest revision as of 15:39, 9 September 2022

Description
After cracking the wifi password in previous challenge, you can now start investigating the traffic in the pcap.
100pts
Question
Analyse the pcap and find the flag.
Solution
Insert wlan password as a WPA-PWD pinkpanther. You will find it at wireshark -> Edit -> Preferences -> Protocols -> IEEE 802.11 -> Decryption keys -> Edit
Then I just start to browse through packets and start with tcp streams. Using "Follow TCP stream" I just did go through streams one by one until I found something interestin. In stream 6 was http answer where was flag base64 encoded. So I decoded that and found that you have to encode it again. Until that I got the flag.
Tools
- wireshark
- echo
- base64
Flag
aee7d6e6-4e05-4fa6-b0cb-a53439b55224