DNS Enum: Difference between revisions
From Pessin randon wiki
Created page with "=== '''Description''' === You have been recruited to conduct audit on company DNS server. You must find out if any internal DNS records are exposed to the public. 80 pts === Question === Conducting DNS enumeration activities to see if you can find anything interesting. Domain to enumerate is dns.ctf P.S. When you find the flag, it's obvious :) === Solution === I performed DNS enumeration as requested: '''dnsrecon -d dns.ctf''' The flag was there. === Flag === ctft..." |
No edit summary |
||
| (One intermediate revision by the same user not shown) | |||
| Line 1: | Line 1: | ||
[[File:DNS enum.png|thumb|DNS Enum]] | |||
=== '''Description''' === | === '''Description''' === | ||
You have been recruited to conduct audit on company DNS server. You must find out if any internal DNS records are exposed to the public. | You have been recruited to conduct audit on company DNS server. You must find out if any internal DNS records are exposed to the public. | ||
| Line 17: | Line 19: | ||
=== Flag === | === Flag === | ||
ctftech{ad4a4091-48ea} | <code>ctftech{ad4a4091-48ea}</code> | ||
===Links=== | |||
*[[CTF Challenges | Back to CTF Challenges page]] | |||
Latest revision as of 12:02, 17 October 2022
Description
You have been recruited to conduct audit on company DNS server. You must find out if any internal DNS records are exposed to the public.
80 pts
Question
Conducting DNS enumeration activities to see if you can find anything interesting.
Domain to enumerate is dns.ctf
P.S. When you find the flag, it's obvious :)
Solution
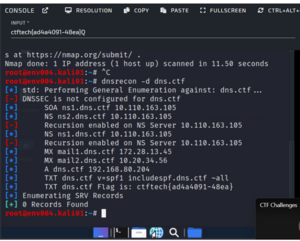
I performed DNS enumeration as requested: dnsrecon -d dns.ctf
The flag was there.
Flag
ctftech{ad4a4091-48ea}