Encoder: Difference between revisions
Created page with "===Description=== This web application allows you to use coding utility to encode and decode base64 100pts ===Question=== Investigate the application, exploit the vulnerability and read the flag from /var/backup/secret.txt ===Solution=== First, I ran a vulnerability scan on the website with the ZAP tool. Unfortunately, nothing was found. Next I tried to enter all kind of commands to both decoder and encoder sides. I realized that especiality I got errors from decoding..." |
No edit summary |
||
| Line 1: | Line 1: | ||
[[File:Encoded-task.PNG|thumb|Encoder task]] | |||
[[File:Encoded-flag.PNG|thumb|Encoder flag + command]] | |||
===Description=== | ===Description=== | ||
This web application allows you to use coding utility to encode and decode base64 | This web application allows you to use coding utility to encode and decode base64 | ||
Latest revision as of 13:59, 13 October 2022
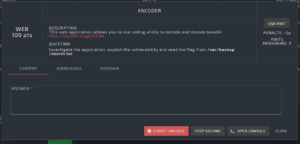
Description
This web application allows you to use coding utility to encode and decode base64
100pts
Question
Investigate the application, exploit the vulnerability and read the flag from /var/backup/secret.txt
Solution
First, I ran a vulnerability scan on the website with the ZAP tool. Unfortunately, nothing was found.
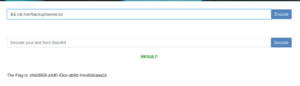
Next I tried to enter all kind of commands to both decoder and encoder sides. I realized that especiality I got errors from decoding side when I was entering commands like include, ls, &&.
I entered similar commands on the encoding side and tried the following command && cat /var/backup/secret.txt
This web page returned a long base64 string that looked nothing like the previous ones. I decoded that string twice and got the task flag for myself.
Tools
- base64
Flag
efa58858-a4d0-43ce-ab8d-44ed5b5aaa1b