Hacked: Difference between revisions
Created page with "===Description=== This web server was defaced by hackers. They made some modification on the system. ===Question=== Admin was able to see from the logs that a SQL database dump was made. Can you find it? Maybe this helps you forward with this incident analysis. ===Solution=== Since we were asked to search for SLQ database dump it makes sense to use gobuster here as well. The command <code>gobuster dir -u [url] -w /usr/share/wordlist/dirbuster/directory-list-2.3-medium...." |
No edit summary |
||
| Line 1: | Line 1: | ||
[[File:Hacked-task.PNG|thumb|Hacked task]] | |||
[[File:Hacked-gobuster.PNG|thumb|Gobuster searching SQL files]] | |||
[[File:Hacked-database.png|thumb|Hacked database dump file]] | |||
===Description=== | ===Description=== | ||
This web server was defaced by hackers. | This web server was defaced by hackers. | ||
Latest revision as of 10:51, 30 September 2022
Description
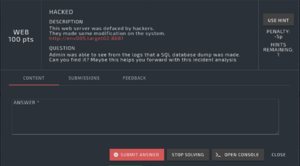
This web server was defaced by hackers.
They made some modification on the system.
Question
Admin was able to see from the logs that a SQL database dump was made.
Can you find it? Maybe this helps you forward with this incident analysis.
Solution
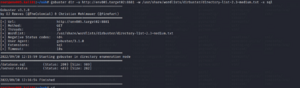
Since we were asked to search for SLQ database dump it makes sense to use gobuster here as well. The command gobuster dir -u [url] -w /usr/share/wordlist/dirbuster/directory-list-2.3-medium.txt -x slq. We find that there is a database.sql file in the root file of the web page. We download this file to the machine using the wget command.
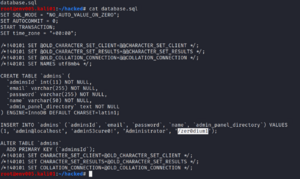
By looking inside this file we can see the database structure. We are interested in both the username, password and admin_panel_directory.
Using the browser, I navigate to the /zer0dium1 folder where we find the task flag.
Tools
- gobuster
- cat
Flag
ctftech{hacked}