PHP Shell code: Difference between revisions
Created page with "===Description=== ===Question=== ===Solution=== ===Tools=== ===Flag=== ===Links=== * Back to CTF Challenges page" |
No edit summary |
||
| (9 intermediate revisions by 2 users not shown) | |||
| Line 1: | Line 1: | ||
[[File:Php-shell-explaned.PNG|thumb|PHP Reverse shell file with comments]] | |||
[[File:Php-shell.PNG|thumb|Cyber cheff with flag]] | |||
[[File:Wireshark-l.PNG|thumb|Wireshark packets]] | |||
[[File:Wireshark-packet.PNG|thumb|Wireshark packet inspection]] | |||
===Description=== | ===Description=== | ||
You have to investigate recent attack on your web server. | |||
Since attackers were very skilled, they used specially designed PHP shell to access the server. | |||
Your friends from Incident Response Department managed to get network capture file with malicious traffic. | |||
Secret flag, which attackers used, is in PCAP file. | |||
All evidences (including php shell code) are here: <nowiki>http://shared.target05/shell_code.zip</nowiki> | |||
200pts | |||
===Question=== | ===Question=== | ||
Can you decrypt web shell command responses? | |||
===Solution=== | ===Solution=== | ||
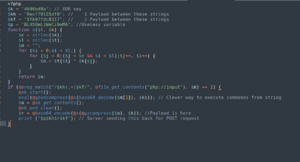
I manually looked through the top php shell file provided and noticed that there was an attempt to hide functions in the file. By sorting them out, I found out how the server and the attacker were working. | |||
So the attacker has sent the following command to a specific file: <code>chdir('/var/www/html');@error_reporting(0);@system('cat flag.txt 2>&1');</code> which he first compresses into a gz package, then performs XOR encryption and converts this to base64. Around this, the attacker wraps an additional identification code to activate the program. | |||
The subtlety of this attack is the use of the eval command, which runs the given command and therefore returns the output of the command executed using the previous encryption method. | |||
The tip here is to remember that the php file in question is run at the server end. | |||
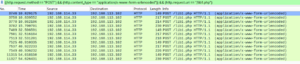
The next step is to open the pcap file with wireshark and see what you can find there. I started by examining what was transferred over the http protocol and exported all the files to disk. After a quick investigation these were of no help. | |||
Next I examined the data sent via the POST method and found a lib1.php file where some interesting data was sent. | |||
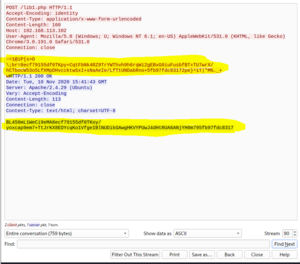
I extracted the packages with wireshark and started to investigate them further. Unfortunately, I didn't realize that I didn't get the response packets included. Wondering about this, I wasted quite a bit of time until I realized that the return message contained the information I needed. I started manually examining the packages until I received the right one. | |||
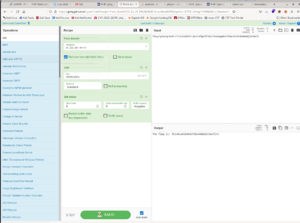
I did a reverse decryption with the Cyber Chef program, copying and pasting the server responses. Before doing that, I had to remove the extra padding around the response that I mentioned earlier ($kh and $kf). The Cyber Chef program also needs to remember to put the XOR key $k. | |||
===Tools=== | ===Tools=== | ||
[https://Unphp.net unphp.net] | |||
Wireshark | |||
PHP | |||
Cyber chef https://gchq.github.io/CyberChef/#recipe=From_Base64('A-Za-z0-9%2B/%3D',true,false)XOR(%7B'option':'UTF8','string':'4696bd9a'%7D,'Standard',false)Zlib_Inflate(0,0,'Adaptive',false,false)&input=VEtveS95b3hjYXA5ZW03K1R0SnJLWDhFRFljcUtvMVZmZ2VJQmxOVURpa0dBd2dIS1ZZUFV3SjRkSHRSVUE2QU5qWUgwbTc5 | |||
===Flag=== | ===Flag=== | ||
<code>fb148ca92d484070b5446b3233eef174</code> | |||
===Links=== | ===Links=== | ||
*[[CTF Challenges | Back to CTF Challenges page]] | *[[CTF Challenges | Back to CTF Challenges page]] | ||
Latest revision as of 18:57, 14 September 2022
Description
You have to investigate recent attack on your web server.
Since attackers were very skilled, they used specially designed PHP shell to access the server.
Your friends from Incident Response Department managed to get network capture file with malicious traffic.
Secret flag, which attackers used, is in PCAP file.
All evidences (including php shell code) are here: http://shared.target05/shell_code.zip
200pts
Question
Can you decrypt web shell command responses?
Solution
I manually looked through the top php shell file provided and noticed that there was an attempt to hide functions in the file. By sorting them out, I found out how the server and the attacker were working.
So the attacker has sent the following command to a specific file: chdir('/var/www/html');@error_reporting(0);@system('cat flag.txt 2>&1'); which he first compresses into a gz package, then performs XOR encryption and converts this to base64. Around this, the attacker wraps an additional identification code to activate the program.
The subtlety of this attack is the use of the eval command, which runs the given command and therefore returns the output of the command executed using the previous encryption method.
The tip here is to remember that the php file in question is run at the server end.
The next step is to open the pcap file with wireshark and see what you can find there. I started by examining what was transferred over the http protocol and exported all the files to disk. After a quick investigation these were of no help.
Next I examined the data sent via the POST method and found a lib1.php file where some interesting data was sent.
I extracted the packages with wireshark and started to investigate them further. Unfortunately, I didn't realize that I didn't get the response packets included. Wondering about this, I wasted quite a bit of time until I realized that the return message contained the information I needed. I started manually examining the packages until I received the right one.
I did a reverse decryption with the Cyber Chef program, copying and pasting the server responses. Before doing that, I had to remove the extra padding around the response that I mentioned earlier ($kh and $kf). The Cyber Chef program also needs to remember to put the XOR key $k.
Tools
Wireshark
PHP
Flag
fb148ca92d484070b5446b3233eef174