Api: Difference between revisions
No edit summary |
No edit summary |
||
| (2 intermediate revisions by the same user not shown) | |||
| Line 1: | Line 1: | ||
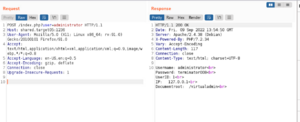
[[File:Admininstrator.PNG|thumb|Burp suite with administrator ]] | |||
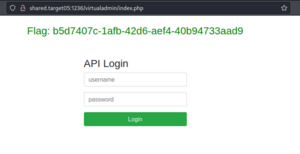
[[File:Flag-api.PNG|thumb|flag after login]] | |||
===Description=== | ===Description=== | ||
We found a nice target where some backed API communication is happeingn behind the scenes at URL. | We found a nice target where some backed API communication is happeingn behind the scenes at URL. | ||
| Line 7: | Line 9: | ||
===Question=== | ===Question=== | ||
Can you reverse engineer messages and extract some information from this endpoint? | Can you reverse engineer messages and extract some information from this endpoint? | ||
===Solution=== | ===Solution=== | ||
| Line 36: | Line 39: | ||
===Flag=== | ===Flag=== | ||
<code>b5d7407c-1afb-42d6-aef4-40b94733aad9</ | <code>b5d7407c-1afb-42d6-aef4-40b94733aad9</code> | ||
===Links=== | ===Links=== | ||
*[[CTF Challenges | Back to CTF Challenges page]] | *[[CTF Challenges | Back to CTF Challenges page]] | ||
Latest revision as of 15:36, 9 September 2022
Description
We found a nice target where some backed API communication is happeingn behind the scenes at URL.
Sometimes it is possible to extrtact valuable information by tampering some parameters.
Some dictionary attack may be used against index.php script and it seems that a web proxy is best tool for this job.
Question
Can you reverse engineer messages and extract some information from this endpoint?
Solution
First I was setting up proxy to investigate what is going on. I used burp suite for that.
Somehow you have to find account name by brute forcing user argument, but you have to pass it in POST request. It still have to be sended as url parameter.
I was trying to use wfuzz but even knowing the correct account I could not be able to setup it correctly.
wfuzz -c -z file,common.txt -u http://shared.target05:1236/index.php?user=FUZZ -d "a=b" --hw 6
I use -d tag to send fuzzin with POST.
When you get your username correctly you will get the login credential
Username: administrator
Password: terminator008
UserID: 1
IP: 127.0.0.1
Documentroot: /virtualadmin
You can go after that with your browser http://shared.target05:1236/virtualadmin/ and you will find login page. When you enter earlier credentials on it you get the flag.
I was extracting webpage with curl command curl -X POST -d "username=administrator&password=termionator008" http://shared.target05:1236/virtualadmin/index.php
Tools
- burp suite
- wfuzz
- firefox
- curl
Flag
b5d7407c-1afb-42d6-aef4-40b94733aad9